Tag: Computers
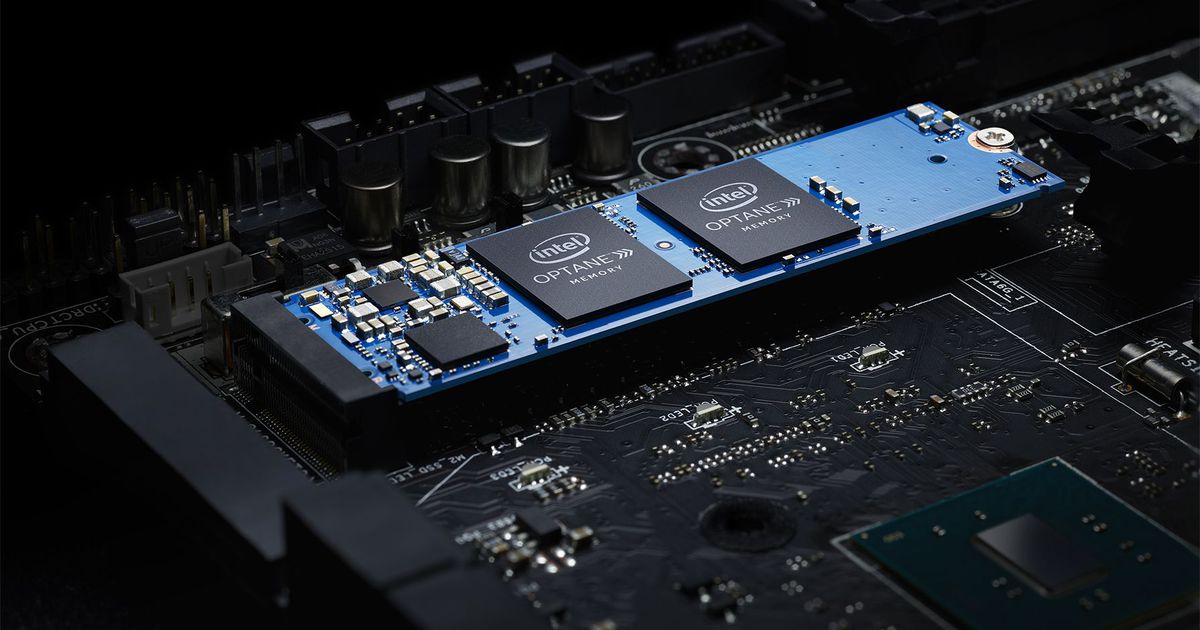
Intel is ready to unleash its super fast secret weapon
Intel is ready to unleash Optane. If you’ve ever waited for a webpage to load, took a lap around the office while your computer rendered 4K video or watched in dismay as your favorite video game stuttered to life, you know that computers are struggling to keep up with all the data. Intel isn’t down […]

Can this Al win a $200,000 poker battle?
An AI system named Libratus will go up against top poker players during matches later this month in Pittsburgh. Image: joe raedle/ Getty Images Artificial intelligence has already become a part of our everyday lives through AI-assisted services like Siri. But Al has its own hobbies too, including the mind-whirling game of poker. Scholars at […]

Physical Cleaning of Computers
by Gwydion M. Williams Having computer equipment regularly cleaned and maintained brings many advantages. Cleaning equipment on a regular basis could extend its lifespan, reduce downtime, create a healthier environment, and improve corporate image. The fan in a PC draws in dust and dirt that could prevent the machine from cooling properly and cause overheating […]

Author points out relationship of humans to computers in new book
ALEXANDRIA, Va. (PRWEB) April 06, 2015 Dr. Mohamed K. Kamara Ph.D. wanted to share his knowledge about the relationship of humans to computers based on the theory of thinking ability through his book, “The Impact of Cognitive Theory on Human and Computer Development” (published by Xlibris). This book explains the impacts of cognitive theory […]

Growing Threat of Cyber Attacks & Quantum Computers Drives the Quantum Cryptography Market, According to a New Report by Global Industry Analysts, Inc.
San Jose, California (PRWEB) April 07, 2015 Follow us on LinkedIn – Quantum Cryptography (QC), a technique that harnesses the quantum-mechanical properties of light for creating secure encryption, is assuming ever more importance in the light of the string of major cyber attacks on government agencies and public utilities. Moreover, the vulnerability of conventional cryptographic […]